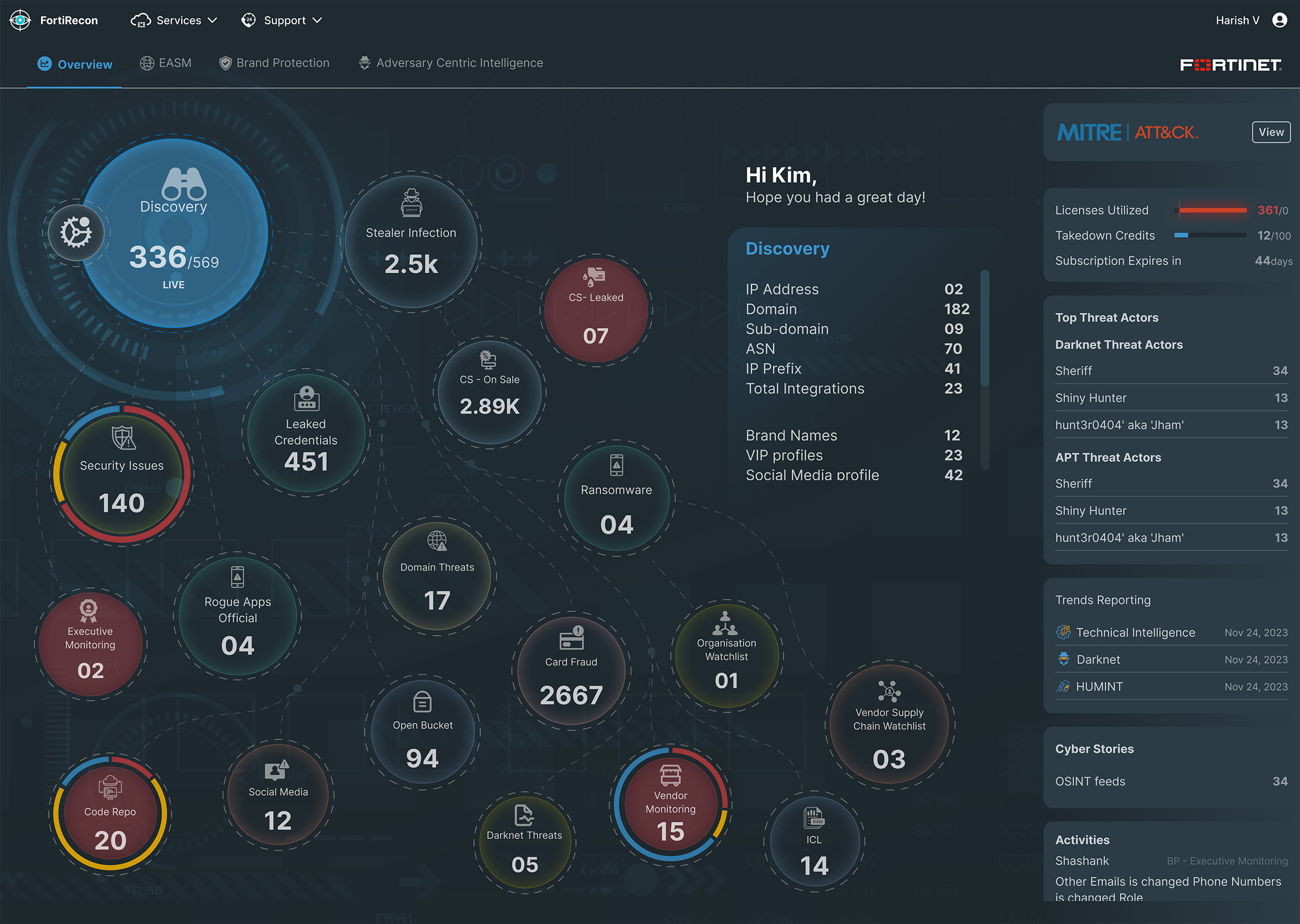
Overview
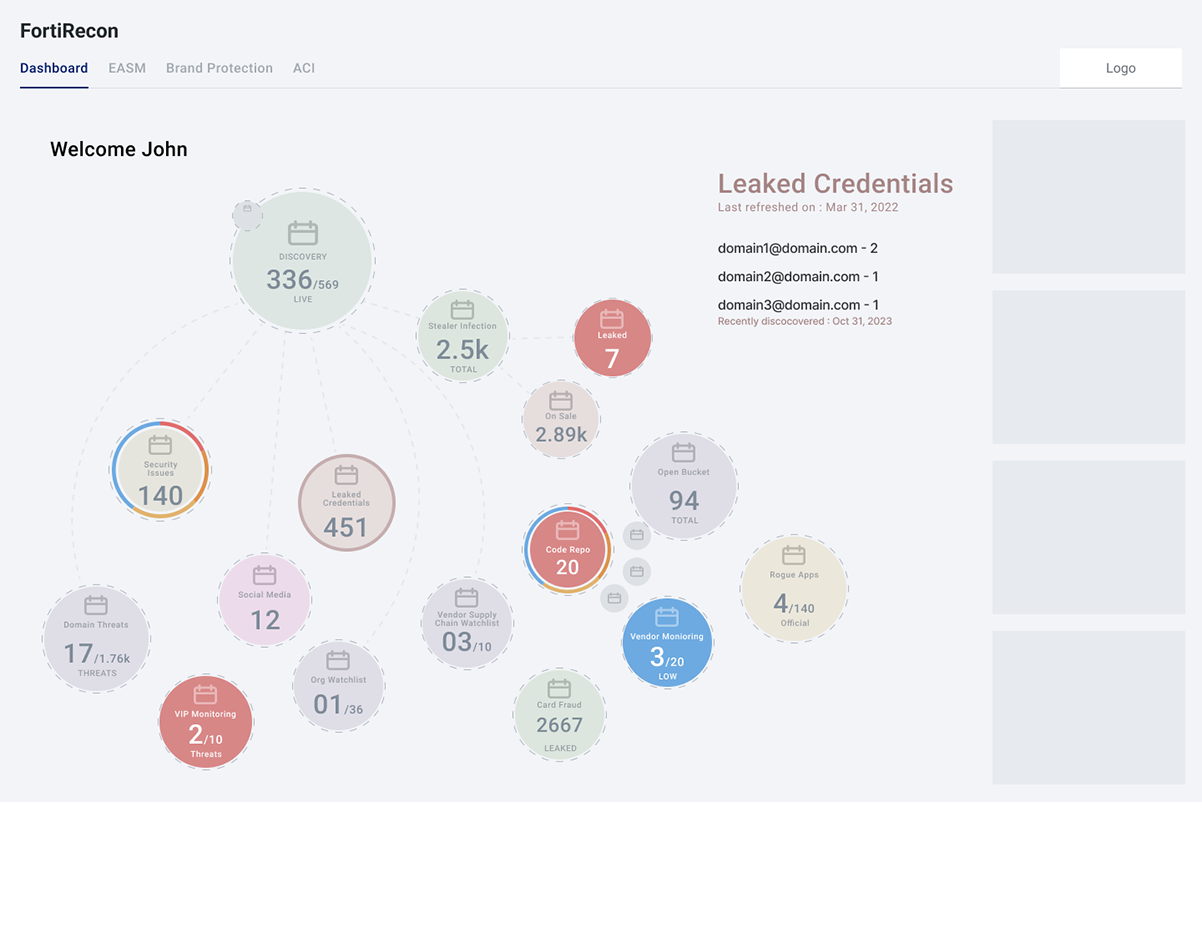
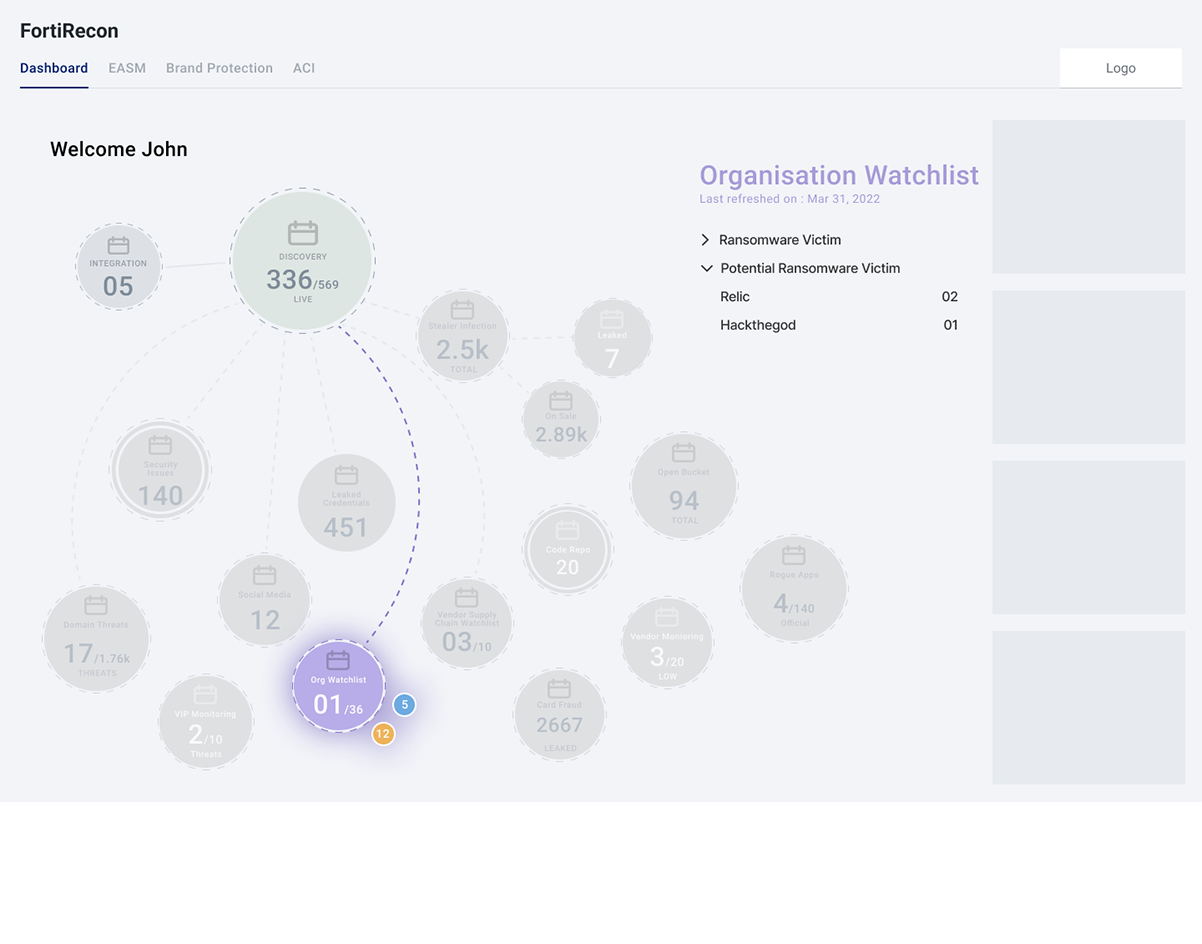
As organizations increasingly rely on digital platforms for their operations, the security of their sensitive information becomes paramount. This includes data spread across various channels such as social media, credentials, domain names, IP addresses, subdomains, financial cards, and mobile applications,etc all of which are critical to business performance.
User Goals
- Swiftly identify the specifics of a data breach - understanding who was responsible, when and how it occurred, and the extent of the data affected.
- The ultimate aim is to effectively recover from the breach and mitigate any potential damage.
Problem Statement
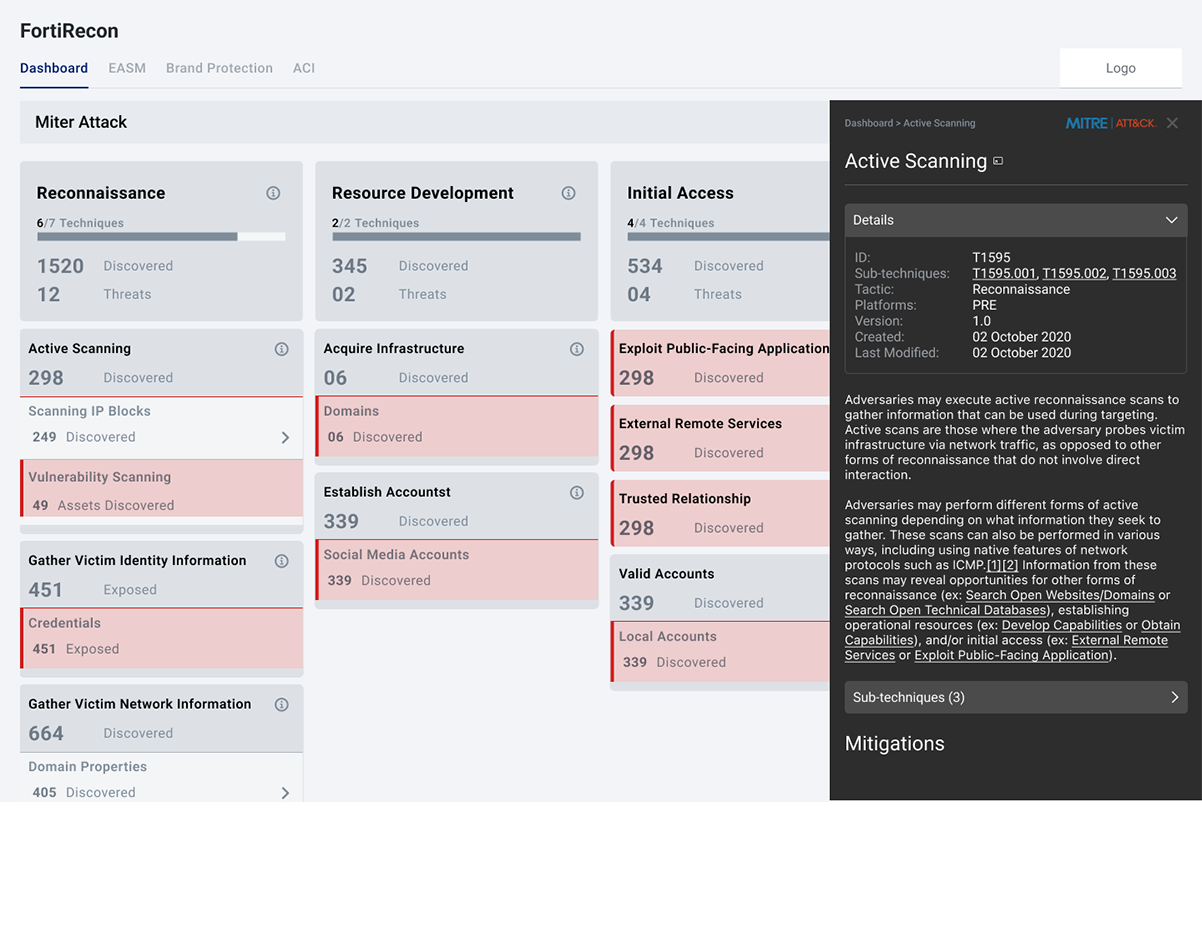
When utilizing the Recon application, organizations are presented with a comprehensive interface designed to track and identify potential data breaches,Phishing, typosquatingetc. However, users encounter significant challenges in pinpointing specific breach details due to the overwhelming volume of data presented.
Painpoints
- Navigating through multiple pages for various data types (social media, credentials, domains, etc.).
- Compiling a comprehensive breach overview is confusing and overwhelming.
- The process is time-consuming, hindering efficient breach identification and recovery.
My role in the project
My role as a UX Designer includes a wide range of responsibilities aimed at ensuring the product not only meets the users' needs but also provides an intuitive, efficient, and engaging experience.
- Research and Analysis
- Strategy and Planning
- Design
- Collaboration with Development Teams
- Validation through testing anf evaluation
- Stakeholder Presentations
Design Timeline
I applied a Lean UX framework, focusing on three iterative milestones over a two-weeks timeline. This approach emphasized swift, structured progress with a continuous feedback loop, ensuring agility and effective collaboration throughout the project.

User Interview
To gain a deeper understanding of the current challenges faced by our clients and to empathize with their experiences, I conducted user interviews with the three clients who provided reviews of our product. The collected data was thoroughly consulted and analyzed to derive insights that would inform the development of the most effective and tailored solutions for their specific needs.
User interview results >
Ideation

Progress Tracking
We have drafted the benefits and Key Performance Indicators (KPIs) to provide a clear overview of how we can measure the effectiveness of our security solution. This will guide us in tracking progress and identifying areas for improvement.

Idea visualization
with the extensive feedback loops and we were involved in transforming our ideas into visual concepts" highlights a collaborative and iterative approach to bringing abstract ideas to life through visual representation.